Why Your Code Needs Protection (And What Happens When It Doesn't)
You’ve spent months, maybe even years, building a brilliant new algorithm. You've poured everything into perfecting the code, setting the stage for a launch you hope will define your company. Then, weeks before your release, a competitor launches a product with eerily similar functionality. This isn't just a bad dream; it's a common reality for innovators who neglect their intellectual property (IP).
Thinking of your code as just a product is a critical mistake. It's a core business asset, the digital equivalent of a factory's most important machine. Not protecting it is like leaving the factory doors wide open overnight. Without proper software IP protection, you are inviting others to walk in and take the very engine that powers your business. The consequences aren't just a few lost sales—they can erode your market position and stop your growth before it even starts.
The Hidden Costs of Negligence
When protection is an afterthought, the costs are steep and often hidden. It’s not just about direct theft. A lack of clear IP ownership spooks investors during crucial funding rounds because they see a business with no competitive shield.
It also tanks your company’s valuation during a potential sale, as buyers see little unique value to acquire. On top of that, you miss out on lucrative licensing opportunities—a powerful way to generate revenue by allowing others to use your protected technology for a fee. The most successful companies don't just build great software; they build a fortress around it from day one.
Protection as a Competitive Weapon
It’s a hard truth that the most dominant companies are not always the most inventive—they are often simply the best protected. They view software IP protection not as a defensive legal chore but as an offensive strategic weapon.
This protection allows them to enter new markets with confidence, block competitors from copying their core features, and build a brand reputation that customers trust. They understand that in a crowded field, a unique idea is only truly valuable as long as it remains unique.
To build an effective defense, you must first understand the battlefield. Intellectual property is a broad field with several distinct tools. Software is particularly complex because a single product can involve multiple types of IP.
| IP Type | What It Protects | Software Example |
|---|---|---|
| Copyright | Original creative works (code, text, UI) | The source code of your application |
| Patent | Novel inventions and processes | A unique method for data compression |
| Trademark | Brand identifiers (names, logos, slogans) | Your software's name and logo |
| Trade Secret | Confidential business information | A secret search algorithm or customer list |
A single product can use all of these. Your code itself is subject to copyright, your unique processes may be patentable, your brand name is a trademark, and your secret algorithms can be protected as trade secrets. Failing to understand these distinctions is a common and costly vulnerability.
This growing awareness of IP's importance is reflected in market trends. The global intellectual property management software market, valued at USD 9.23 billion in 2023, is projected to soar to USD 28.17 billion by 2032. This explosive growth shows that businesses are increasingly investing in tools to manage and defend their digital assets. Discover more insights into the IP market growth. Protecting your creations is no longer optional; it's a fundamental part of building a modern, defensible business.
The Four Protection Pillars Every Developer Should Master
Thinking of software IP protection as a single, one-size-fits-all shield is a common mistake. It’s better to imagine it as a fortress with four distinct walls: copyrights, patents, trade secrets, and trademarks. Each one protects a different part of your creation, and learning how to use them together is the key to building a truly secure business asset.
The image below illustrates how these different IP types can exist within a single product, from the code itself to the formal legal documents that protect it.
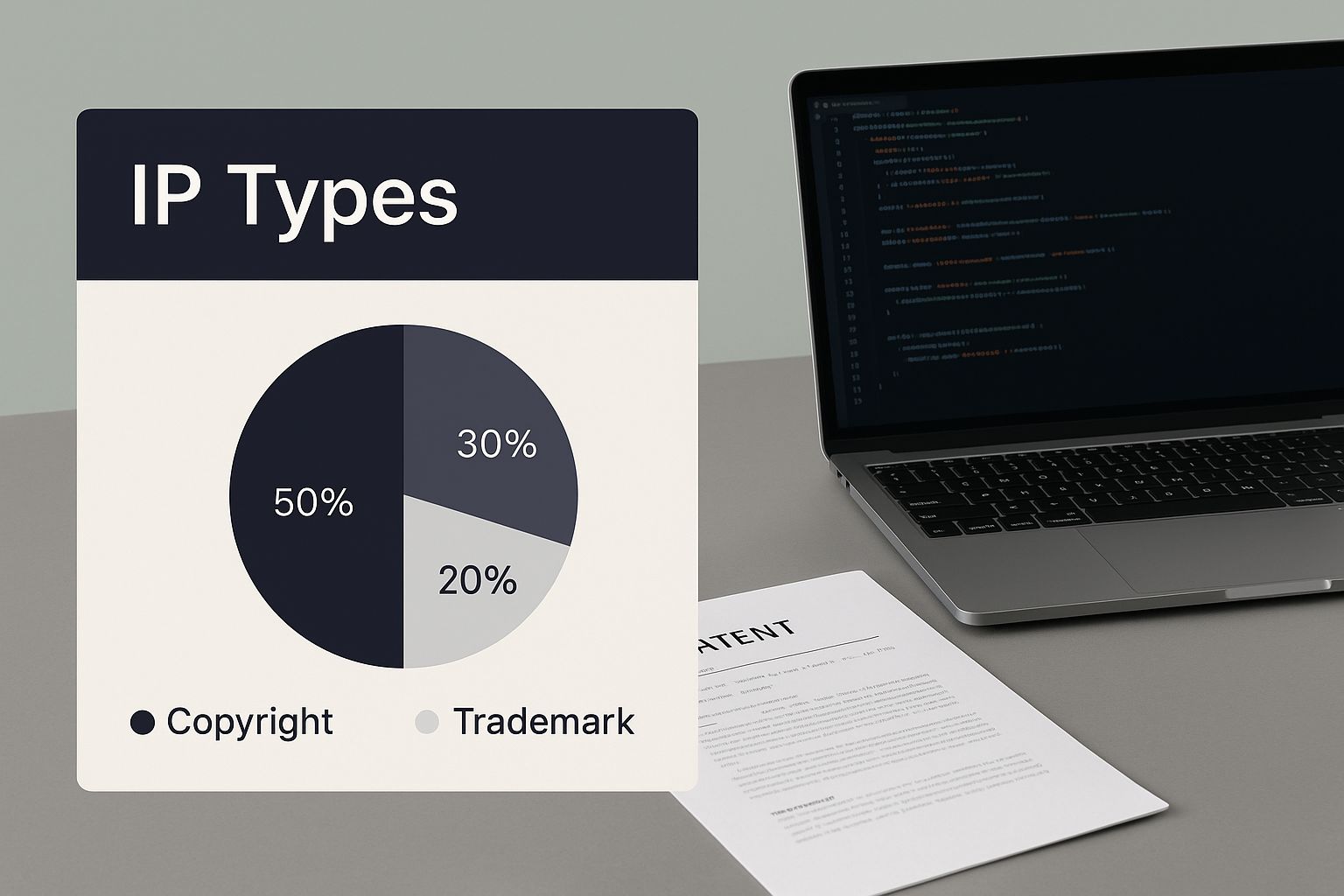
This shows that a software product is really a bundle of different intellectual property assets, and each one needs its own protection plan. Before we dig into each one, it helps to see how they stack up against each other. The table below breaks down the key differences in cost, time, and strength to help you choose the right tools for your specific situation.
Smart Software IP Protection Strategy Comparison
Real-world analysis of protection methods showing costs, timeline, effectiveness and practical implementation for different software scenarios
| Protection Method | Implementation Time | Realistic Costs | Protection Strength | Best Applications | Common Pitfalls |
|---|---|---|---|---|---|
| Copyright | Automatic upon creation; formal registration takes 3-9 months. | $45-$65 for online registration. | Moderate: Protects literal code, not the idea. | Source code, object code, UI/UX design, documentation. | Thinking copyright protects the underlying functionality; failing to register before an infringement. |
| Patent | 2-5+ years for application and grant. | $15,000 – $30,000+ (including legal fees). | Strong: 20-year monopoly on the invention. | New algorithms, unique software processes, system architecture. | The high cost and long wait time; invention not being truly "novel" or "non-obvious." |
| Trade Secret | Immediate, with ongoing effort. | Varies (legal fees for NDAs, security system costs). | Potentially indefinite, but fragile. | Proprietary algorithms, customer data, internal formulas. | Accidental disclosure; not taking "reasonable steps" to maintain secrecy. |
| Trademark | Common law rights are immediate; federal registration takes 9-18 months. | $250-$750 per class (filing fee) + legal fees. | Strong: Protects brand identity in the marketplace. | Software name, logos, taglines. | Choosing a name that's too generic; failing to monitor for infringement. |
As you can see, there’s no single ‘best’ option. The strongest IP strategy often involves a mix-and-match approach, using copyright for your code, a trademark for your brand, and perhaps a patent or trade secret for your core innovation.
Copyright: The Automatic Foundation
Copyright is the bedrock of software protection, and it automatically applies to your work the moment you create it. It covers your source code, object code, and user interface designs. However, it only protects the specific expression of your idea—the literal lines of code you wrote—not the functional concept behind it.
Think of it like a cookbook. Copyright protects the exact wording of the recipe and the photos, but it doesn't stop someone else from using the same list of ingredients to bake a cake using their own instructions.
While that automatic protection is a nice safety net, you should always formally register your copyright. Registration is required before you can file an infringement lawsuit, and it allows you to claim significant statutory damages and attorney’s fees. It's what gives your copyright real teeth.
Patents: Protecting the Unique Process
While copyright guards your code's written form, a software patent protects the actual functionality or process your code executes. This is a much higher level of protection reserved for methods or systems that are genuinely new. To qualify, your invention must be novel, non-obvious, and useful.
For instance, you couldn't patent the general idea of online shopping, but you might be able to patent a new, inventive process for one-click purchasing that dramatically improves server efficiency. Getting a patent is a long and expensive journey, but it grants a powerful 20-year exclusive right, preventing anyone else from making, using, or selling your invention.
Trade Secrets: The Power of Confidentiality
Some of your most important intellectual property might be something no one outside your company ever sees. A trade secret is any confidential business information that gives you a competitive advantage. This could be a proprietary search algorithm, a unique dataset, or a specially curated customer list. The legendary formula for Coca-Cola is a perfect example of a trade secret that has lasted for over a century.
Unlike patents, trade secrets don't have an expiration date and don't require government registration. Their protection is entirely dependent on your ability to keep them secret. This means actively using non-disclosure agreements (NDAs), implementing strict digital and physical access controls, and having clear security policies.
Trademarks: Guarding Your Brand Identity
Finally, trademarks are all about protecting your brand's reputation in the marketplace. This includes your software's name, logo, and slogans—the unique identifiers that distinguish your product from the competition. A trademark ensures that when customers see your brand, they know the quality and origin of the product they're getting.
The primary body for this in the U.S. is the United States Patent and Trademark Office (USPTO), the federal agency responsible for granting patents and registering trademarks.

This official resource is the essential starting point for formalizing your patent and trademark rights within the United States. A smart software IP protection strategy integrates these four pillars, creating a layered defense tailored to your business needs and goals.
Software Patents: When They Work (And When They Don't)
Software patents are often considered the holy grail of intellectual property. They grant a powerful 20-year monopoly on a specific function or process, creating a serious and long-lasting shield against competitors. Think of it this way: copyright protects your specific lines of code, but a patent can protect the very method your code uses to achieve a result. However, this power comes with a great deal of complexity, expense, and risk, making it a high-stakes decision not suitable for every piece of software.
What Makes a Software Innovation Genuinely Patentable?
Not every clever idea in software can be patented. The U.S. Patent and Trademark Office (USPTO) has strict criteria, particularly after the landmark Alice Corp. court case tightened the rules against patenting abstract ideas that are simply run on a generic computer. To earn a patent, your software must represent a specific, concrete invention, not just a concept.
The two main hurdles you must clear are:
- Novelty: Your invention has to be brand new and not previously shared with the public in any form.
- Non-Obviousness: It must be more than just a simple, logical next step for someone with average skill in your field. It needs to be a real inventive leap.
For instance, the general idea of matching users on a social platform is an abstract idea and can't be patented. But, if you develop a new algorithm that uses a unique machine learning model to improve matching accuracy in a technically distinct way, that might be patentable. This fine line is a central challenge in modern software IP protection, and understanding it is essential.
The Demanding Reality of the Patent Application Process
Getting a patent is a marathon, not a sprint. The entire journey from filing an application to having a patent granted can easily take 2 to 5 years and set you back tens of thousands of dollars in legal fees. A critical early step is the prior art search, where you or your attorney must comb through existing patents and publications to confirm your idea is truly new. Skipping this or doing a poor job can lead to rejection years down the line.
Tools like Google Patents provide a way to start exploring the millions of existing patents.

This interface gives a glimpse into the huge database that needs to be checked to verify an invention's uniqueness before filing. The complexity of this process has fueled a growing market for management tools. The global intellectual property software market was valued at $7.5 billion in 2022 and is expected to reach $31.3 billion by 2032, showing just how much companies are investing to manage these important assets. Read the full research on the IP software market here.
When a Trade Secret Is the Smarter Play
Given the high cost, long wait, and public disclosure required for a patent, it isn't always the right move. When you file for a patent, you have to describe your invention in enough detail to teach others how to make it. Once your 20-year term is up, that information is free for anyone to use. This is where trade secrets present a strong alternative.
If your competitive edge comes from a process that isn't easily discovered by looking at your final product (reverse-engineered), keeping it a trade secret could offer stronger protection that potentially lasts forever.
Choosing the right path means weighing your strategy carefully:
| Consideration | Choose Patent | Choose Trade Secret |
|---|---|---|
| Discoverability | High (easy for others to figure out) | Low (hard to figure out from the product) |
| Desired Lifespan | 20 years is enough | Protection needed for the long term |
| Budget | High (can cover application costs) | Lower (costs are mainly for security) |
| Disclosure | You are okay with teaching the public | Your advantage depends on secrecy |
Ultimately, a software patent is a specialized tool in your software IP protection toolkit. It's most valuable for foundational, non-obvious technologies that form the core of your competitive advantage. For many other software innovations, a practical mix of copyright and trade secret protection provides a more flexible and cost-effective defense. For a deeper look into building a multi-layered and effective defense, learn more in our article about intellectual property for software.
Copyright Protection That Actually Protects Your Work
One of the most powerful, yet often misunderstood, parts of protecting your software is copyright. The moment you write a line of code and save the file, you automatically own the copyright. While that sounds like a solid defense, relying on automatic protection alone is like locking your front door but leaving every window in the house wide open for a competitor to climb through.
The Power of Formal Registration
While copyright ownership is automatic, it lacks real enforcement power until you formally register it with the U.S. Copyright Office. Registration is what transforms your basic ownership claim into a powerful legal tool. Without it, you can't even file a lawsuit to stop someone from stealing your code.
More importantly, registering your work before an infringement happens (or within three months of its publication) makes you eligible for statutory damages and attorney's fees. This is a massive advantage, allowing you to seek compensation up to $150,000 per willful infringement without the difficult task of proving the exact financial harm you suffered.
This government portal is the gateway to securing the strongest possible legal standing for your creative work. It turns your copyright from a passive right into an active, defensible asset.
Strategic Copyright Registration Guide for Software
To help you plan your approach, this practical roadmap shows the benefits, timelines, costs, and necessary paperwork for registering different types of software projects.
| Software Type | Registration Timeline | Investment Required | Protection Benefits | Essential Documentation |
|---|---|---|---|---|
| Mobile App (v1.0) | Before public launch | ~$65 (online fee) | Secures statutory damages eligibility; establishes a public record of ownership. | First and last 25 pages of source code; screenshots of key UI screens. |
| SaaS Platform | Within 3 months of a major update | ~$65 per version | Protects new features and codebases; strengthens your position against competitors. | Deposit of identifying portions of the new code; description of new features. |
| Internal Enterprise Tool | Upon completion of core development | ~$65 | Prevents departing employees from claiming ownership or reusing the code. | Complete source code deposit (if trade secrets are not a concern). |
| Open Source Project | Before initial release | ~$65 | Defines your ownership and the terms of the license you are granting to others. | Source code and a copy of the chosen open source license (e.g., MIT, GPL). |
The key insight here is that registration is a small, proactive investment that secures a massive defensive advantage, regardless of your project's scale.
Establishing Clear Ownership from Day One
One of the biggest copyright pitfalls is unclear ownership. If you hire freelancers or use contractors, who owns the code they write? Unless you have a signed work-for-hire agreement that explicitly transfers copyright ownership to your company, the developer who wrote the code legally owns it. This can lead to disastrous and expensive legal disputes down the line.
Your development process must be built to maintain a clear chain of title for every single line of code. This involves:
- Employee Agreements: Make sure all employment contracts clearly state that any code written as part of the job is the company's property.
- Contractor Agreements: Always use strong work-for-hire contracts that assign all IP rights to your company before any work begins.
- Code Repository Logs: Keep detailed logs that show who contributed what and when. This creates a clear, timestamped record of creation that is invaluable in any potential dispute.
It's also important to remember that copyright protects the literal code, not the brand name itself. For a clear breakdown of these distinct protections, you might be interested in our guide on trademark vs. copyright. Understanding this difference is fundamental to a complete IP protection strategy.
Licensing: Maintaining Control While Enabling Growth
Your copyright gives you the exclusive right to reproduce, distribute, and create derivative versions of your code. A license is simply your permission for others to use your software under specific conditions that you define. This tool is where you maintain strict control while enabling business growth and collaboration. For commercial software, an End-User License Agreement (EULA) dictates what users can and cannot do.
The world of open source software also revolves entirely around licensing. Using an open source library in your project means you are bound by its license terms. Some licenses, like the MIT license, are very permissive. Others, like the GNU General Public License (GPL), have a strong "copyleft" provision. Think of it as a "pay it forward" rule that could legally require you to make your own source code public if you incorporate their code into your distributed product. A proactive IP protection approach involves diligently auditing all third-party code to ensure license compliance and protect your proprietary work.
Trade Secrets: Your Hidden Competitive Advantage
While patents and copyrights are public declarations of ownership, some of the most valuable software IP protection comes from the things nobody outside your company ever sees. Think of a trade secret as your company’s secret recipe—the legendary formula for Coca-Cola is a perfect example. It's a unique algorithm, process, or collection of data that gives you an edge, and its power comes entirely from being kept confidential.
Protecting it isn’t a one-time filing; it's an active, ongoing process. This screenshot from Wikipedia shows the internationally recognized conditions that information must meet to be considered a trade secret.

The main point is that this protection isn't granted automatically. The information must have commercial value because it is secret, and you, the owner, must be taking reasonable steps to keep it that way.
What Qualifies as a Software Trade Secret?
Not all company secrets can be legally protected as a trade secret. For a piece of your software IP to qualify, it has to pass a three-part test. It must have commercial value, it can't be common knowledge, and most importantly, you have to prove you’re actively trying to keep it under wraps.
For software companies, potential trade secrets are hiding in plain sight. They often include things like:
- Proprietary Algorithms: A one-of-a-kind data analysis or sorting algorithm that makes your app’s killer feature possible.
- Source Code for Key Modules: The specific code that runs your most important backend functions.
- Customer and Data Compilations: A carefully assembled customer list or dataset that a competitor would love to have.
- Internal Tools and Processes: Custom deployment scripts or testing methods that make your team more efficient than others.
The key distinction is that a trade secret protects the confidential information itself, offering a different, but just as powerful, shield as other forms of IP.
Implementing Practical Confidentiality Systems
Maintaining a trade secret is like building a fortress around your information. This isn't just about technology; it's about creating a culture of confidentiality backed by clear, provable systems. The strength of your trade secret protection depends entirely on these proactive efforts.
Key steps to implement include:
- Strict Access Controls: Use role-based digital permissions. Not every engineer needs to see the source code for your core algorithm. Access should be granted on a “need-to-know” basis, with logs to track who sees what. Don't forget physical security, like locked server rooms.
- Robust Employee and Contractor Agreements: This is your first line of defense. Anyone with potential access must sign a Non-Disclosure Agreement (NDA). Your employment contracts should also include strong confidentiality clauses that remain in effect even after someone leaves the company.
- Clear Documentation and Labeling: Make it a habit to mark sensitive documents, code files, and internal communications as “Confidential.” This simple act serves as a constant reminder and provides powerful evidence that you intended to maintain secrecy if a legal dispute ever occurs.
- Ongoing Employee Education: Your team can’t protect what they don’t understand. Regularly train your staff on what trade secrets are, why they matter, and what their personal responsibility is in safeguarding them.
Balancing Secrecy with Collaboration
A common worry is that tight security around trade secrets will slow down work and prevent collaboration. If every piece of information is locked away, how can teams build anything together? The goal isn't to create a paranoid work environment but to find a smart balance.
This means being deliberate about segmenting your information. For instance, you can design your codebase so that the core, secret algorithms are contained within a tightly controlled module. The rest of your developers can then use this module through a well-defined API without ever needing to see the source code itself.
This approach protects your most valuable assets while still allowing your team to collaborate freely on other parts of the application. Effective software IP protection is about intelligent control, not a total lockdown, and finding this balance is essential for growing your team and technology without giving away your competitive advantage.
Building Your Protection Strategy (Without Breaking Your Budget)
Protecting your software's intellectual property is more about being smart than being rich. You don’t need an enterprise-level budget to get started. For startups and growing companies, the secret isn't to protect everything, but to protect what truly drives your business forward. Think of it like drawing a map before a long road trip; it ensures you use your limited resources—time and money—to build a fortress around your most valuable digital creations.
This creates a scalable plan that works with your development cycles and business goals, not against them.
Conducting a Practical IP Audit
Before you can protect your assets, you have to know what you have. This is where an IP audit comes in. It’s like taking a detailed inventory of your home's valuables before you buy a security system. You wouldn't put an alarm on an empty room, so you first need to identify what’s actually worth protecting. This process shines a light on both your crown jewels and your potential weak spots.
A practical audit boils down to a few key steps:
- Asset Identification: Make a systematic list of everything. This includes your source code, unique algorithms, UI/UX designs, and even branding elements like your company logo.
- Ownership Verification: Confirm who legally owns each piece. Was it built by a full-time employee under contract, or by a freelancer who never signed a proper work-for-hire agreement? This is a common and costly mistake.
- Value Assessment: Sort each asset by its importance. Is it a core, revenue-generating feature or a minor part of the software that could be easily replaced?
For businesses with a global reach, organizations like the World Intellectual Property Organization (WIPO) offer incredible resources for this.
WIPO's portal provides tools and information on international treaties that help you manage and protect your IP in different countries—a critical step for any software with users around the world.
Prioritizing Your Protection Efforts
Once your audit gives you a clear inventory, it’s time to prioritize. You can’t afford to wrap every single asset in the most expensive legal protection, and frankly, you don't need to. It’s about making smart choices. You wouldn’t put steel bars on your bathroom window before securing the front door. The same logic applies to your software IP protection.
Focus your budget by looking at two critical factors:
- Business Impact: How essential is this piece of IP to your competitive edge? Your one-of-a-kind recommendation engine is far more critical to protect than the design of your settings page.
- Risk of Exposure: How easily could a competitor copy or reverse-engineer this asset? A hidden back-end process is naturally less exposed than a user-facing interface feature.
By concentrating your efforts on high-impact, high-risk assets first, you ensure your budget is spent where it matters most.
Budgeting for Growth and Ongoing Management
Your protection plan should grow with your company. A boot-strapped startup has very different needs and financial constraints than a publicly-traded corporation. Begin with cost-effective, high-impact actions. For less than a hundred dollars, you can formally register your copyright, which provides immense legal leverage if someone copies your code. Similarly, having solid NDAs and employment agreements costs little upfront but can prevent massive legal headaches down the road.
As your company grows and secures funding, you can start to budget for more expensive protections, like patenting a truly foundational piece of technology. This isn't just a one-time setup; it's an ongoing process of tracking, maintaining, and re-evaluating your assets. This kind of strategic financial planning is key to building a resilient business. For more on how to weave these legal steps into your broader strategy, check out our related article on essential business legal advice.
When Protection Becomes Worth Fighting For
Getting your copyrights, patents, and trade secrets is a huge accomplishment, but it's only half the job. Think of these legal rights as a shield. It's great to own one, but it won't do you any good if you don't know how to use it when someone takes a swing at you.
A solid software IP protection plan needs a clear strategy for enforcement. This is where the law books meet the balance sheet, and deciding when to fight can be as important as the software you created.
The Economics of Enforcement: Fight, Negotiate, or Walk Away?
Deciding to enforce your IP isn't just about being "right." It's a business calculation, plain and simple. A full-blown patent infringement lawsuit can cost hundreds of thousands, if not millions, of dollars. Before you go on the offensive, you have to weigh the potential gains against the very real costs in time and money.
It's like deciding whether to file an insurance claim after a fender bender. You wouldn't go through the hassle for a tiny paint scratch, right? The paperwork and potential rate hike just aren't worth it. But for a major collision, you absolutely would.
You need to ask yourself some tough questions about any IP infringement. Is the other party a small-time player or a major competitor eating into your sales? Can your company afford a legal battle that might drag on for years? Is the IP they're using a core part of your business, or just a minor feature? Your answers will tell you if a legal fight is a smart move or a costly mistake.
Cost-Effective Monitoring and Initial Response
You can't stop a threat you don't know exists. That’s why consistent monitoring is the bedrock of any good enforcement plan. The good news is that this doesn't have to break the bank. You can set up an effective early-warning system with a few simple techniques.
Here are some practical, low-cost steps to start with:
- Set up automatic alerts for your software's name, unique features, and brand slogans.
- Routinely search app stores and code repositories for anything that looks or works suspiciously like your product.
- Use reverse image search to spot anyone using your UI designs, logos, or other graphics without permission.
When you spot a potential problem, you don't have to jump straight to a lawsuit. The most common and powerful first step is sending a cease-and-desist letter. This is a formal notice from an attorney that clearly states your rights and demands the other party stop their infringement. It’s a strong opening move that often resolves the issue without ever going to court.
Balancing Aggression with Strategic Business Goals
Staying up-to-date on how IP cases are playing out in court can give you a major advantage. Platforms like Lexology offer daily news on IP lawsuits and enforcement trends.
Keeping an eye on these developments helps you see how judges are thinking and which strategies are working. This knowledge proves that the most aggressive move isn't always the smartest one. Instead of starting a fight, you could try negotiating. A licensing deal can turn an infringer into a paying customer, opening up a brand new revenue stream.
Sometimes, the best choice is to do nothing at all. If an infringement is minor, doesn't really threaten your business, and would cost a fortune to fight, your money is better spent on developing your product and finding new customers. A good enforcement strategy is about precision, not just power.
It also means actively managing your IP portfolio by renewing your most valuable assets and letting go of those that no longer fit your business goals. Making these critical decisions takes experience. At Cordero Law, we help you create an enforcement plan that defends your work without emptying your bank account. We'll guide you on when to fight, when to talk, and when to put your energy somewhere else.
If you're ready to create an IP strategy that is both strong and smart, contact Cordero Law today to ensure your assets are prepared for any challenge.
